Weak Telnet Remote Access on PIX-LINK LV-WR22 (CVE-2024-46280)
Vulnerability Information:
- Product: PIX-LINK
- Model: LV-WR22
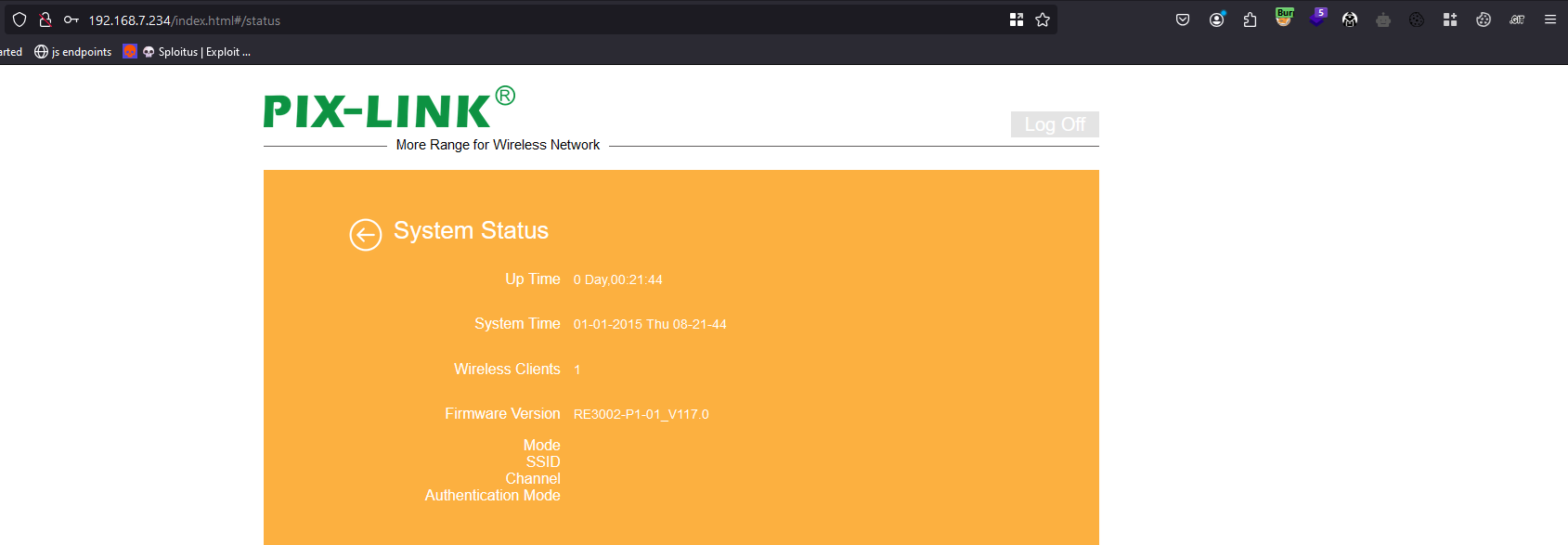
- Firmware Version: RE3002-P1-01_V117.0
- Vulnerability: Weak Telnet Remote Access
- Impact: Root access to the device via the local network.
- Author: Red Team - Miguel Alves (@0xmupa), Fabrício Oliveira (xf5), Sérgio Charruadas
Hello friend, today I’m showing you a vulnerability that I found while researching the PIX-Link LV-WR22 router, although it’s critical, it’s quite easy to exploit.
The vulnerability consists of a misconfiguration on the part of the firmware developers in the telnet configuration and the consumer is unable to change the telnet password without technical knowledge.
Firmware Version:
PoC:
Accessing telnet via its default port (port 23) we are asked for the username and password.
When I saw that I immediately thought…

GOTCHA!!!!
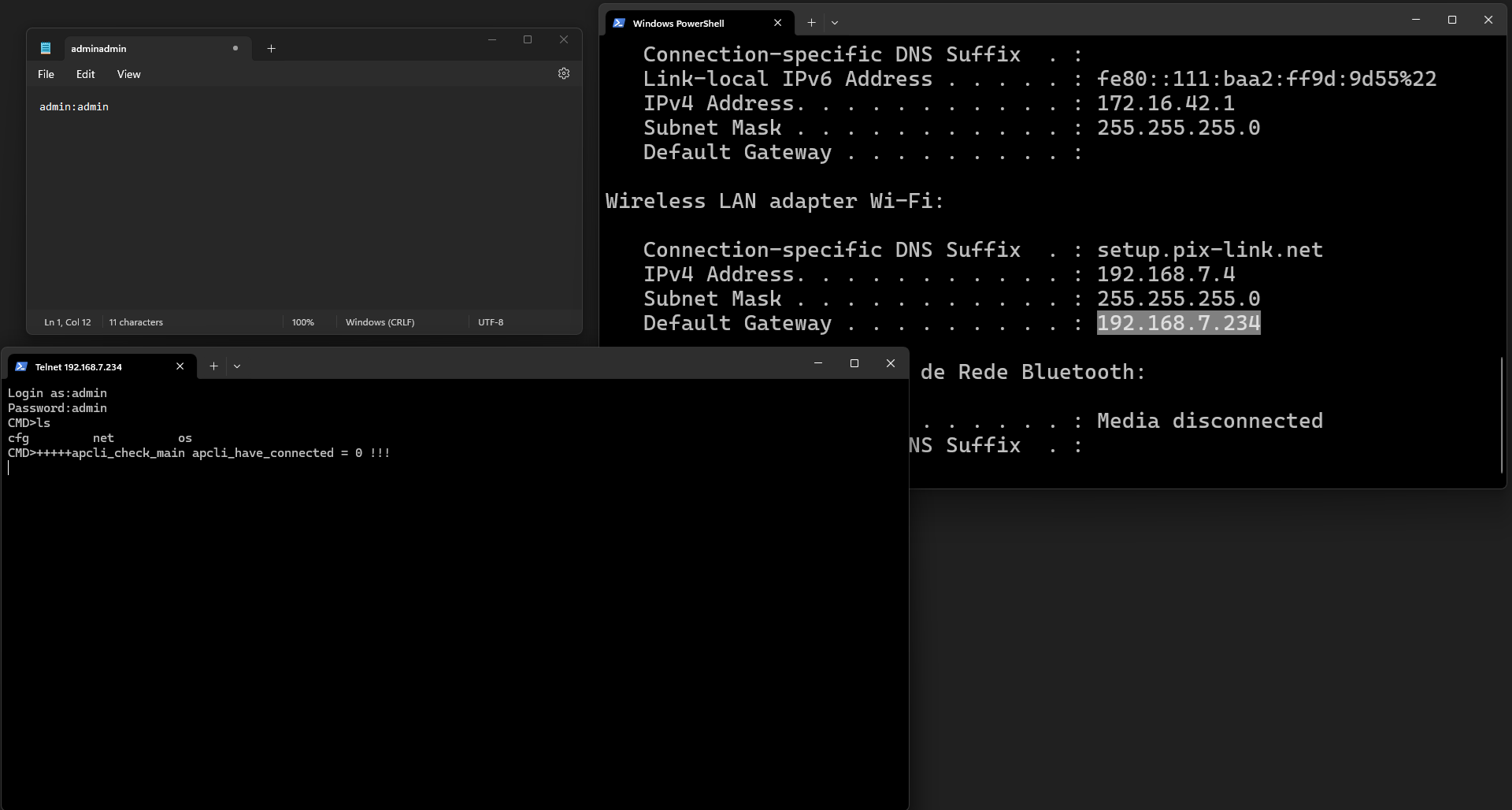
Although it’s a rather stupid vulnerability, it’s a vulnerability that we see in many systems today.
Growth hackers don’t tolerate waste.
- Ryan Holiday
